*This entry was originally written in Japanese in the past based on AWS WAF Classic.
Table of Contents
- Introduction
- Relationship between Conditions and Filters in AWS WAF
- Combinations of Condition types and Filters you can use
- Details of each item you can use in Filters
- How AWS WAF rules work in terms of Conditions and Filters
- Rule samples for when you operate AWS WAF
- Conclusion
Introduction
In Part 2 of this series, we will explain the relationship between Conditions and Filters. If you haven’t read Part 1 Basic Structure yet, you could understand the topics discussed in this post better by reading Part 1 beforehand.
- Part 1: AWS WAF Classic Explained - Basic Structure
- Part 2: AWS WAF Classic Explained - Relationship between Conditions and Filters (this post)
- Part 3: AWS WAF Classic Explained - Structure of string and regex matching and examples usage
Relationship between Conditions and Filters in AWS WAF
Conditions are used to specify limitations to allow or block requests on AWS WAF. We will use Filters to set specific details like string match conditions and parts of requests to match.
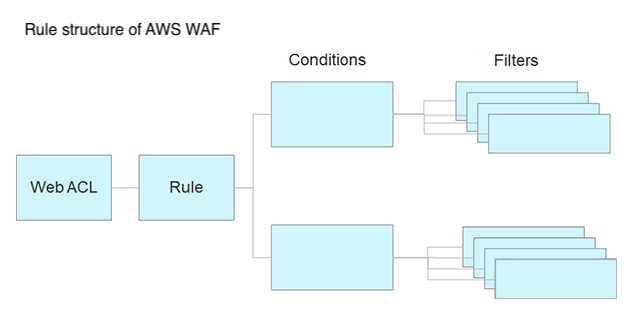
Combinations of Condition types and Filters you can use
| Condition | Filters you can use |
|
Cross-site scripting match conditions A condition that allows or blocks based on requests that appear to contain malicious scripts |
|
|
IP match conditions A condition that allows or blocks based on the IP addresses that the requests originate from |
|
|
Geo (Geographic) match conditions A condition that allows or blocks based on the countries that the requests originate from |
|
|
Size constraint conditions A condition that allows or blocks based on the length of specified parts of requests |
|
|
SQL injection match conditions A condition that allows or blocks based on requests that appear to contain malicious SQL code |
|
|
String match conditions A condition that allows or blocks based on strings that appear in the requests |
|
|
Regex match conditions A condition that allows or blocks based on strings that match a regular expression (regex) pattern in the requests |
|
IP address conditions and geographic match conditions are pretty straightforward in the list; their regulations are based on IP addresses and countries. The other conditions require you to use Filters to specify where the condition should match. Let’s take a look at the details of each item in filters.
Details of each item you can use in Filters
- Part of the request to filter on
- Transformation
- IP addresses
- Location type
- Size (Bytes)
- Comparison operator
- Match type
- Value to match
- Regex patterns to match to request
1. Part of the request to filter on
Choose the part of each HTTP request to inspect from below.
| Type | Description |
| Header | HTTP header like User-Agent |
| HTTP method | HTTP method like GET and POST |
| Query string | Part of a URL that appears after "?" character Example: ?aaa=Tokyo&bbb=Yokohama |
| Single query parameter (value only) | A parameter in a query string Example: ?aaa=Tokyo&bbb=Yokohama |
| All query parameters (values only) | All parameters in a query string Example: ?aaa=Tokyo&bbb=Yokohama |
| URI | URI path of the request which identifies the resource |
| Body | Body of the HTTP request |
*Attackers could insert malicious content in various places like query, body, and headers. It does not necessarily mean that the attacks could succeed, but it surely is suspicious access, so it is recommended to specify several values in conditions.
2. Transformation
Set transformations (ex. decoding) to apply before inspecting the request by AWS WAF Classic.
| Type | Description |
| None | No transformations |
| Convert to lowercase | Converts uppercase letters to lowercase |
| HTML decode | Decodes HTML-encoded characters |
| Normalize whitespace | Transform characters like line breaks and tabs to space characters |
| Simplify command line | Deletes characters like \ " ' ^ and replace characters like ; to space characters |
| URL decode | Decode a URL-encoded request |
3. IP addresses
Set the IP address range you want to use in IP addresses conditions using CIDR notation.
There is a point to pay attention to.
AWS WAF Classic supports IPv4 address ranges: /8 and any range between /16 through /32. AWS WAF Classic supports IPv6 address ranges: /24, /32, /48, /56, /64, and /128.
4. Location type
It is used for geography match conditions and can only be Country.
5. Size (Bytes)
It is used in size constraints conditions. Set the length in bytes of query strings you want AWS WAF Classic to inspect.
6. Comparison operator
It is used in size constraints conditions. Choose a comparison operator for the threshold you set in Size (Bytes) from below.
| Type | Description |
| Equals | Equals the value set in Size (Bytes) |
| Not equal | Doesnot equal the value set in Size (Bytes) |
| Greater than | Greater than the value set in Size (Bytes) |
| Greater than or equal | Greater than or equal to the value set in Size (Bytes) |
| Less than | Less than the value set in Size (Bytes) |
| Less than or equal | Less than or equal to the value set in Size (Bytes) |
7. Match type
It is used in string match conditions to set where the strings to match will appear in “Part of the request to filter on.”
| Type | Description |
| Contains | The string to match appears anywhere in the specified part |
| Exactly matches | The string to match and the value in the specified part of the request are identical |
| Starts with | The string to match appears at the beginning of the specified part of the request |
| Ends with | The string to match appears at the end of the specified part of the request |
| Contains word | The string to match is included in the specified part of the request and only contains alphanumeric characters and underscore |
*For example, in URIs, you could specify certain file extensions or specify a condition like begin with part of the path (ex. /wp-admin/).
8. Value to match
Set the value to inspect in HTTP requests by AWS WAF Classic.
*In string match conditions, the maximum length is 50 bytes. For regex match conditions, the maximum length is 70 bytes.
9. Regex patterns to match to request
Set the regex pattern to inspect in HTTP requests by AWS WAF Classic.
For official information, refer to the page below.
Creating and configuring a Web Access Control List (Web ACL)
How AWS WAF Classic rules work in terms of Conditions and Filters
We went over each element so far. Lastly, let’s take a look at how AWS WAF Classic rules work.
In AWS WAF Classic rules, they 1. evaluate filters, 2. evaluate conditions, and 3. decide the action.
OR/AND conditions change depending on the filters or conditions.
Also, note that behaviors change according to the order.
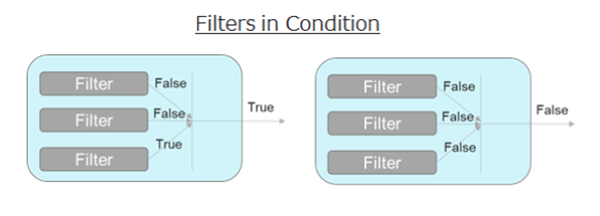
1. Filters’ evaluations
Filters in conditions are evaluated by OR condition.
Thus, matching one of the filters in a condition will result in TRUE for the condition.
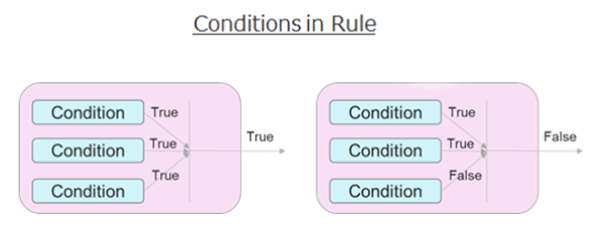
2. Conditions’ evaluations
Conditions in rules are evaluated by AND condition.
Thus, all the conditions in a rule have to match to result in TRUE for the condition.
Conditions must be specified with “does match” or “does not match.”
3. Deciding the action
Action (Allow, Block, or Count) is decided when a rule is TRUE.
Rules are evaluated in order and terminate the evaluation once there is a TRUE statement.
If the action is Count, the evaluation moves to the next rule.
The default action (Allow or Block) will be taken if a request does not match any rules.
Please note that if the default action is not set to Allow, the request may be terminated.
Rule samples for when you operate AWS WAF
We have created sample rules that can also be used in an actual environment based on what we’ve gone through in this post.
| Order | Rules | Action | Condition | Filter |
|---|---|---|---|---|
| 0 | Whitelist | Allow | IP Match | 1. IP Adress |
| 1 | ManualIPBlockRule | Block | IP Match | 1. IP Adress |
| 2 | LargeBodyMatchRule | Count | Size Constraint | 1.Size Constraint |
| 3 | SqliRule | Block | SQL Injection |
|
| 4 | XssRule | Block | Cross-Site Scripting |
|
Example structure of the rules above
1. Whitelist (Allow)
Add a trustworthy requester who completes administrative tasks.
Avoid adding a wide range of IP addresses (ex. IP addresses in Japan) in case of attacks.
2. Blacklist (Block)
Add IP addresses that try to access even if you block them, wasting the resources. Check the IP address information using WHOIS, just in case. If the clients (your target requesters) are all located in Japan, consider blocking requests from overseas.
3. Catch suspicious accesses with large requests (Count)
It depends on the architecture of your website, but large requests could contain malicious codes and be suspicious, so detect the access using Count mode.
4. SQL Injection (Block)
- Detect in HTML-decoded body
- Detect in URL-decoded body
- Detect in HTML-decoded query
- Detect in URL-decoded query
- Detect in URL-decoded URI
5. Cross-site scripting (Block)
- Detect in HTML-decoded body
- Detect in URL-decoded body
- Detect in HTML-decoded query
- Detect in URL-decoded query
- Detect in URL-decoded URI
You might want to leave some capacity in case of emergencies to set exclusion rules. If you have enough budget, allocating a spot to include managed rules as part of the rules is also recommended.
Conclusion
We hope you deepened your understanding of conditions and filters in AWS WAF Classic.
If you can utilize conditions and filters, you can prevent various attacks yourself!
In the next post, we will look at string and regular expression matching.
Next post: AWS WAF Classic Explained: Part 3 Structure of string and regex matching and examples usage




