Updates from 06/01/2023
This post has been revised from the WafCharm update.
Updates from 03/23/2023
This post has been revised due to the release of the new WafCharm feature Credential Store.
You can use the access key/secret key method we have been providing, but we recommend using AssumeRole.
Refer to the blog posts below for details on using AssumeRole.
- About Credential Stores
- About AssumeRole configuration and IAM policy
- How to switch to AssumeRole from access key/secret key
Contents:
- 1. Access permissions required to use WafCharm (Managed Policy)
- 2. Attaching Custom Policy to AWS WAF
- 3. Attaching Custom Policy to S3
- 4. Summary
1. Access permissions required to use WafCharm (Managed Policy)
1-1. Open the service page of IAM.
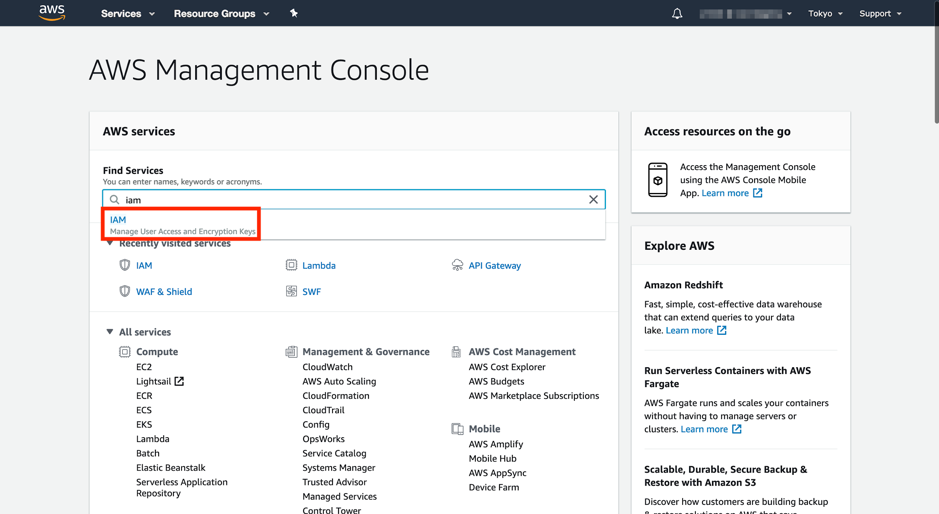
1-2. On IAM's service page, select "Users" from the submenu bar.
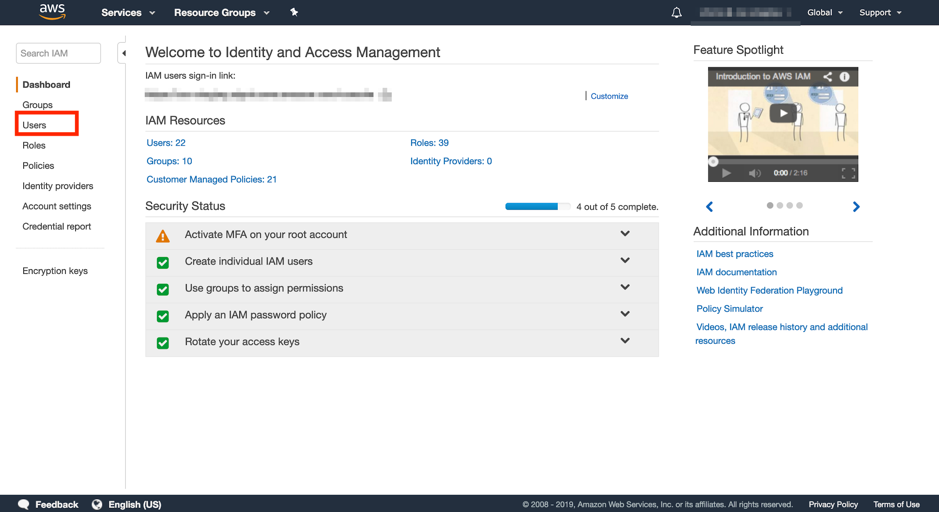
1-3. Click on the AWS WAF user registered on WafCharm.
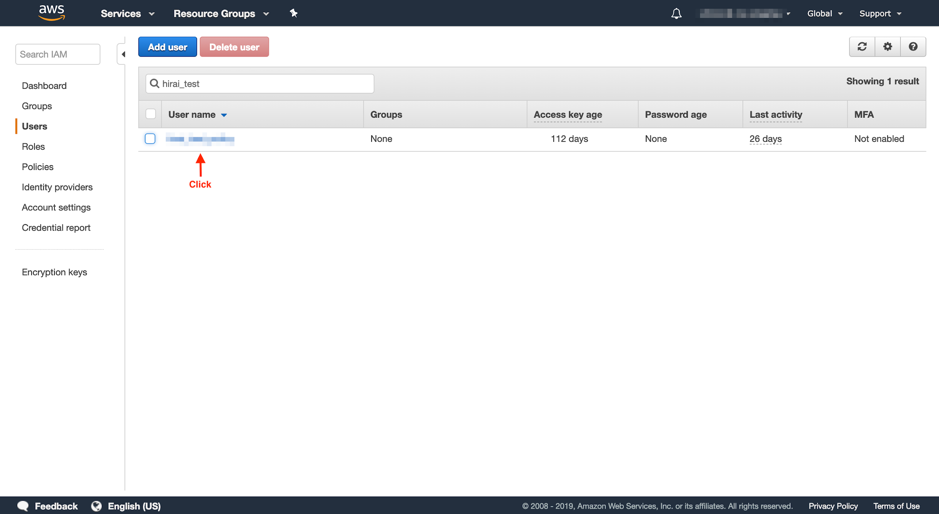
1-4. Make sure that "AWSWAFFullAccess," "AmazonS3ReadOnlyAccess," and "CloudWatchReadOnlyAccess" exist in the attached policy as shown below.
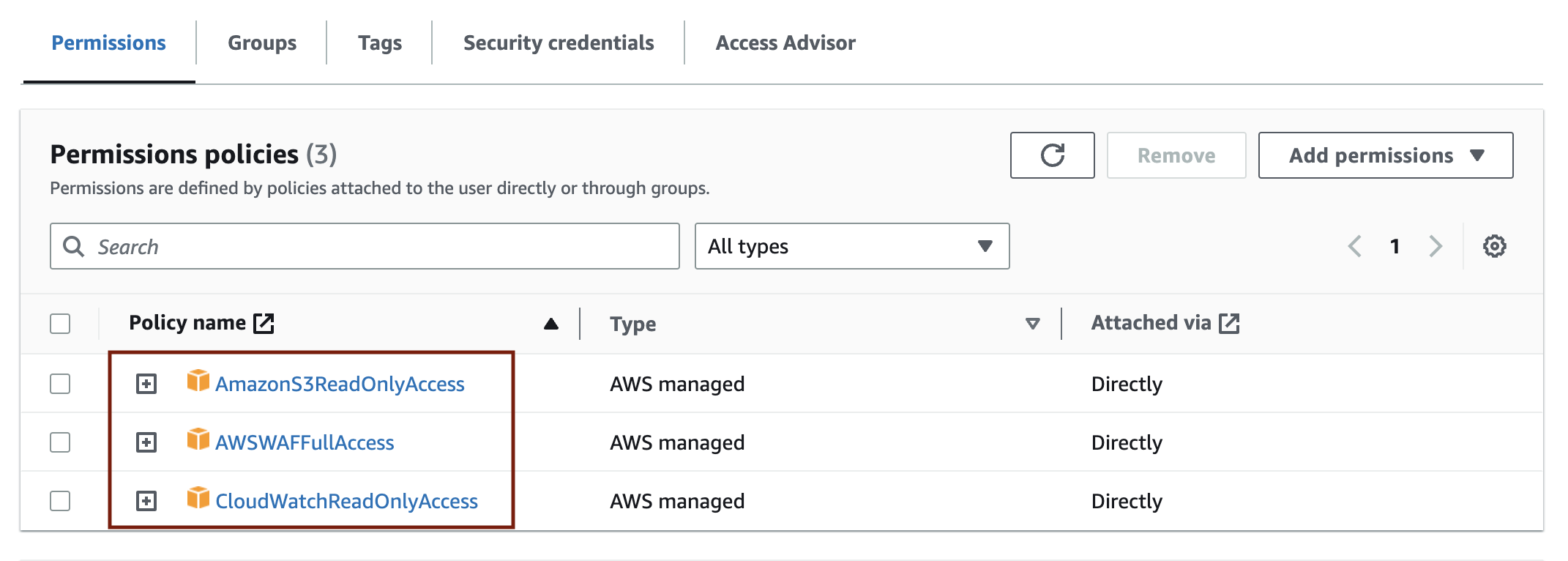
If these three Managed Policies are attached, you can use WafCharm without any issues.
In addition, if you want to grant S3 read permission only for specific Bucket, Prefix, you can change the following JSON according to the environment and use it as Custom Policy of S3.
*As of March, 2023
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:List*",
"s3:Get*"
],
"Resource": [
"arn:aws:s3:::<BucketName>",
"arn:aws:s3:::<BucketName/folder_name>/*"
]
}
]
}
If you want to further limit the permission given by the IAM policy "CloudWatchReadOnlyAccess," use the JSON below as custom policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "cloudwatch:GetMetricData",
"Resource": "*"
}
]
}
2. Attaching Custom Policy to AWS WAF
Please use AWSWAFFullAccess for AWS WAF v2 because feature releases and updates could cause insufficient permission.
3. Attaching Custom Policy to S3
Those who don't want to attach "AmazonS3ReadOnlyAccess" Policy, please attach the following Policy to the S3 registered in WafCharm.
Just a few policies are needed in the Policy of S3.
| GetObject |
| ListBucket |
※As of March, 2023
4. Summary
This time we introduced AWS WAF & S3 access permissions required to use WafCharm.
With the addition of AWS WAF functions, we will continue to update the functions of WafCharm.
Since necessary policies may increase in the future, we recommend attaching Managed Policy.



