Table of Contents
1. Introduction
AWS WAF announced on July 20th, 2023 that URI paths aggregation key for rate-based rules is now available.
Previously, rate-based rules only accepted items such as headers and Cookies as keys to aggregate (also known as custom keys). Now, URI paths have been added to the custom keys.
Although scope-down statements for URI paths have been available, users were required to create multiple rules to track requests for multiple URI paths. With this change, a single rule can track multiple URI paths.
How to use rate-based rules
You can now specify detailed conditions in rate-based rules
2. Configuration
Select [Custom keys] under the [Rate-limiting criteria] in a rate-based rule.
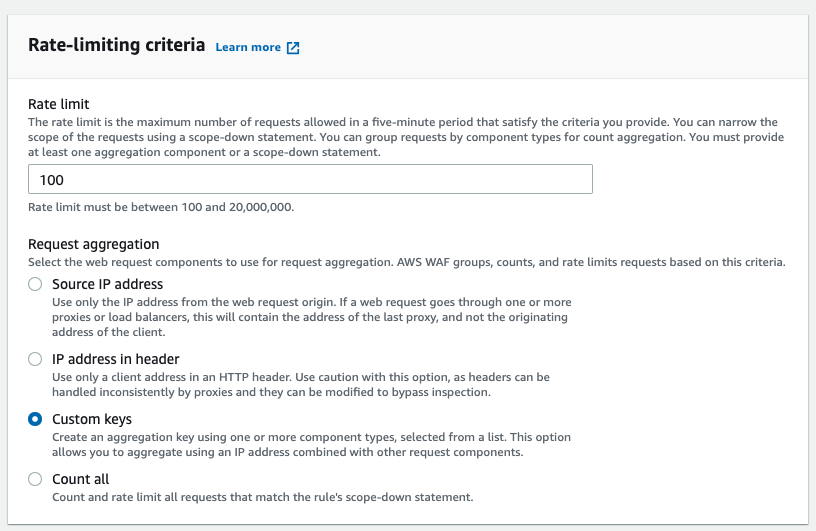
Select the [URI path] option available under the [Request aggregation key] field to use the URI path as a custom key.
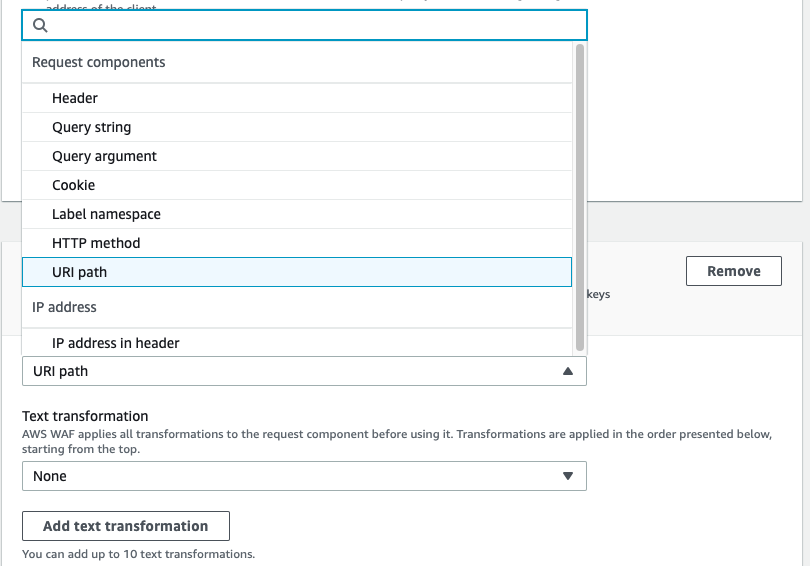
You can click on the [Add a request aggregation key] button to create a rate-based rule with multiple conditions.
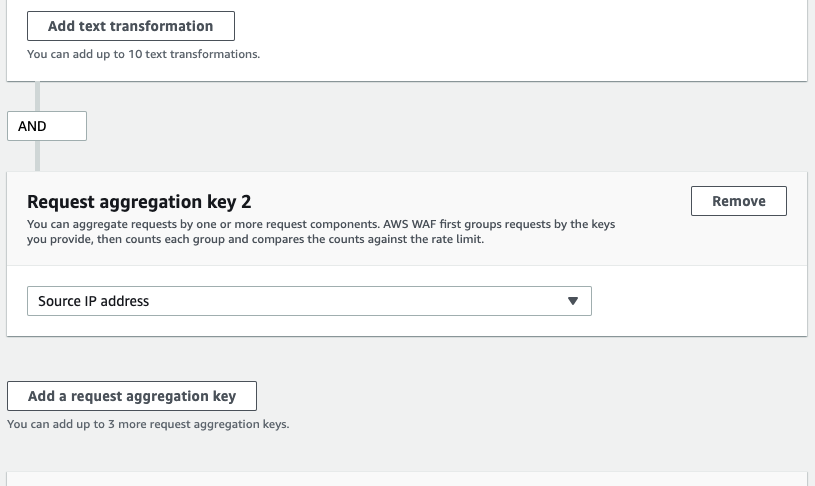
This feature can be interpreted as creating conditions to aggregate the request.
{
"Name": "rate-based-rule",
"Priority": 0,
"Action": {
"Block": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "rate-based-rule"
},
"Statement": {
"RateBasedStatement": {
"Limit": "100",
"AggregateKeyType": "CUSTOM_KEYS",
"CustomKeys": [
{
"UriPath": {
"TextTransformations": [
{
"Type": "NONE",
"Priority": 0
}
]
}
},
{
"IP": {}
}
]
}
}
}
If you use the rule in JSON format above, the requests are aggregated based on the same URI path and the same IP addresses.
You can also add a scope-down statement to narrow down the conditions.
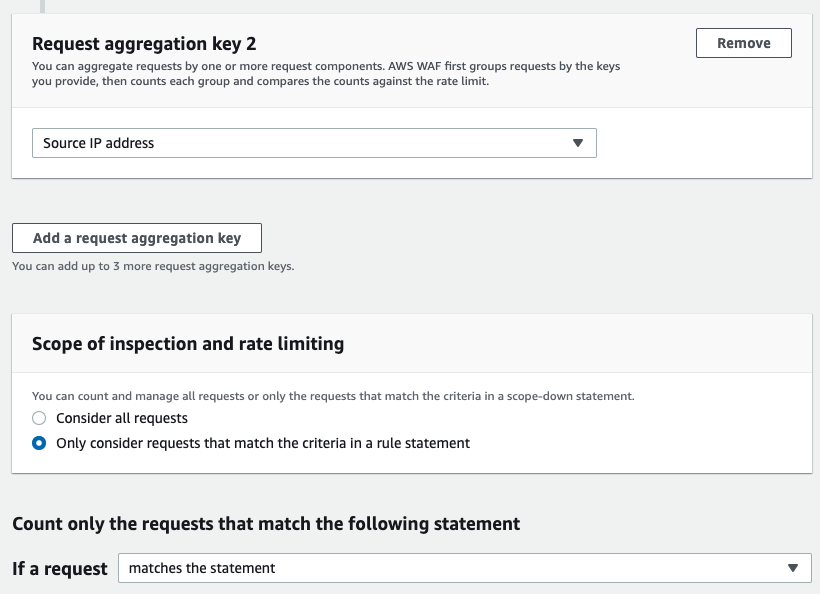
3. Use Case
Since the requests can be aggregated based on URI paths, you can use the custom key to track multiple URI paths individually, such as [/contact/XXX] and [/contact/YYY] instead of using scope down statement on URI path [/contact] to track requests.
The requests must reach the threshold to be detected, but you can use the rule action COUNT to understand the trend of attacks as well. URI paths may not be a suitable condition to use when trying to understand the trends, but specifying URI paths and IP addresses as custom keys to block suspicious requests might be useful once you've analyzed the attacks.
4. Conclusion
This update only consists of an addition of the URI path in the custom key, and the update itself is quite simple. However, there are multiple ways to specify rate-based rule conditions, and it is a complex rule to create.
WafCharm can apply rate-based rules as part of the customization service, so please contact us if you are considering adding rate-based rules.




