【Table of contents】
-
1. Introduction
-
a) What is a firewall?
In the IT industry, a firewall is a "network security system that controls (block or permit) incoming and outgoing communications based on predetermined security rules".
In most cases, dedicated appliances are configured and installed as firewalls at the boundary between the internal and external environments, such as the connection between LANs and WANs, or between separate LANs.
In general, the IP address and port number determine whether a firewall can block the communication. It is almost always used to allow communication to a server on the network, or conversely to prevent it from communicating.
Also, WAF (Web Application Firewall) and IPS (Intrusion Prevention System) are often confused with firewall. Let’s take a look at their differences.
-
b) What is WAF (Web Application Firewall)?
A WAF (Web Application Firewall) is a firewall that is specifically for web applications.
Traditional firewalls use IP addresses and port numbers as a means of deciding whether to block the network traffic or not. However, as Internet evolved and with everyone now able to access it easily, there was a need to take all possible measures against ever increasing cyber-attacks, especially a need for a WAF to protect the application layer, which is a layer above the IP addresses and port numbers.
WAF is able to check the contents of the communication in the web application and block any malicious or unauthorized communication.The benefits of implementing WAF are as follows.
・A defensive measure against unrepairable vulnerabilities found in web applications
・A temporary defensive measure against fixable vulnerabilities found in web applications.
・Able to counter diversified cyber-attacksOf course, web application technology is evolving every day, so it's not a perfect countermeasure against vulnerabilities and attacks. However, by installing a WAF, you can take precautions as a security measure for your web applications. For users running web servers in particular, a WAF is an essential requirement.
-
c) What is IPS (Intrusion Prevention System)?
An intrusion prevention system (IPS) is a form of network security and threat prevention tool, that examines network traffic to detect and prevent identified threats.
There is also a similar system called Intrusion Detection System (IDS), which monitors the network traffic to see if there is any malicious or unauthorized traffic.
As the name suggests, an IDS only detects the malicious traffic, whereas IPS goes one step further to prevent it.
IPS can be broadly divided into the following two categories, depending on the target of intrusion prevention.
・NIPS(Network-type IPS)
→Installed at the boundary of a network, it monitors and protects the traffic that passes through it.
・HIPS(Host-type IPS)
→Installed in the computer acting as a server, it monitors and protects the traffic sent and received by the server.The advantage of NIPS is that it does not need to be deployed on individual servers or computers and can monitor the entire network.
HIPS, on the other hand, has the advantage of being able to monitor even the configuration part of the computer, such as defending against OS-level attacks and software vulnerabilities or monitoring files that you do not want to change or update and preventing changes.
Depending on your requirements for IPS, it is important to consider which of the above two is more appropriate before implementing it onto your system.
-
-
2. Difference between a firewall, WAF and IPS
We've explained what a firewall, WAF, and IPS are so far, but some of you may still be confused about the differences between them. They are all systems that allow network traffic to pass through or be blocked, but broadly speaking, the main difference is the different layers each of them protects.
・Firewall: Decides whether to permit or block the network traffic based on IP addresses or port numbers.
・WAF: Decides whether to permit or block the network traffic based on the contents of communication on the application layer.
・IPS: Monitors traffic that travel across the OS and network to prevent unauthorized communications and changes.
-
a) When do you need a firewall, WAF or IPS?
A firewall is a system that determines whether to permit or block the network traffic based on IP addresses and port numbers.
Therefore, it corresponds to needs such as not wanting access to a particular server or port in the network or wanting only a particular server to be accessible.
Firewalls are often installed at the border between LANs and WANs, or at the connections between LANs.In contrast, WAF's main purpose is to protect web applications.
In case of web applications, communication control based on IP addresses and port numbers may not be able to prevent cyber-attacks. For example, in case of a web server, IP addresses and port numbers (often 80 or 443) are allowed access. However, attacks such as SQL injection and cross-site scripting, which use web forms and other forms to insert specific strings, cannot be prevented beyond the availability of access to the web server.
WAF is effective against such attacks. WAF checks even the contents of the web application, so it is possible to detect and block the kind of communication that seems to be an attack as described above.If you use a web server, you should definitely consider installing WAF.
IPS is more broadly defined as a system for the protection of communications that appear to be malicious on the network. Since WAF's specialties are limited to web applications, it cannot protect the OS, network, or software.
For example, IPS is better at DDoS and attacks with specific software vulnerabilities.
In addition, you can choose between network and host type IPS, depending on the target you want to protect.
-
b) Can't we just implement either one of the Firewall, WAF, or IPS?
Firewalls, WAFs, and IPS have different layers of expertise as follows.
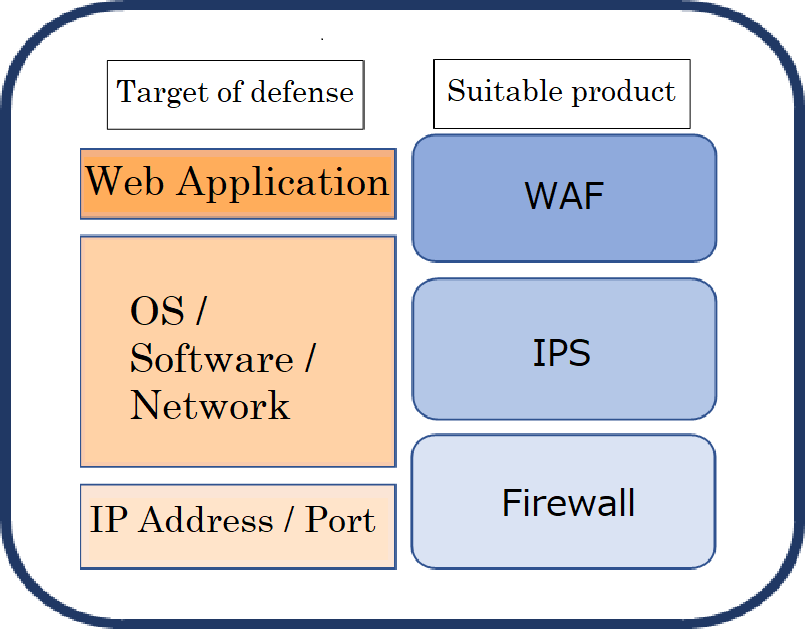
Therefore, it is not always safe to introduce only just either one of them.
For example, a firewall is not enough to completely defend a web application, and a WAF is not enough to detect attacks on the OS itself. You need to know how many servers on your system needs what kind of protection, and then implement the appropriate protection.
-
-
3. Conclusion
In this blog, we explained the differences between a firewall, WAF and IPS.
All three of the above have the same goal of protecting against unwanted traffic, but the devices required to protect specific parts of the system are different.
Before implementing, make sure to list your requirements and take appropriate security measures.





