This post was originally published in Japanese in the past.
Table of Contents
- 1. Introduction
- 2. What is AWS Global Accelerator?
- 3. Attaching to ALB
- 4. Testing results
- 5. Conclusion
1. Introduction
On August 28th, 2019, AWS announced that AWS Global Accelerator Now Supports Client IP Address Preservation for Application Load Balancer Endpoints.
In this post, we tested if IP filtering feature works on WAF by attaching GA (Global Accelerator) to ALB (Application Load Balancer).
2. What is AWS Global Accelerator?
It is a service that improves the performance and availability of applications for users all over the world. It provides static IP addresses that act as fixed entry points for single or multiple AWS regions' application endpoints such as Application Load Balancer, Network Load Balancer, and Amazon EC2. It improves TCP and UDP traffic performance by using AWS Global Network to optimize paths from users to applications. AWS Global Accelerator continuously monitors the condition of application endpoints, detects abnormal endpoints, and redirects traffic to functioning endpoints within a minute.
You can update endpoints without users changing anything and improvements in performance can be expected from optimization.
Such features could be in demand in services that can be influenced by latencies or disaster countermeasures.
Refer to the documents below for the official information.
AWS Global Accelerator
AWS Global Accelerator features
3. Attaching to ALB
First, let's create AWS Global Accelerator.
Click the [Create Accelerator] button.
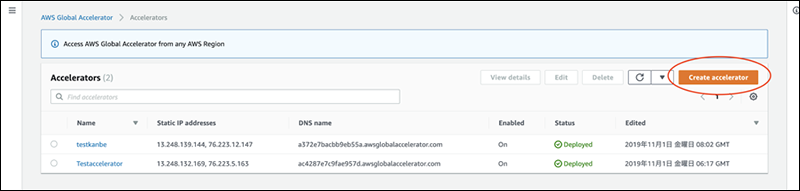
Enter a name and select IPv4 under the IP address type.
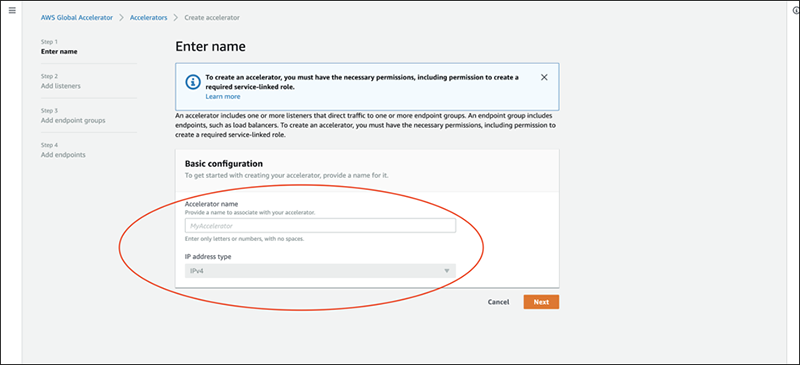
Next, select port and protocol.
In this test, we will set them as below.
- Port: 80, 443
- Protocol: TCP
- Client affinity: Default
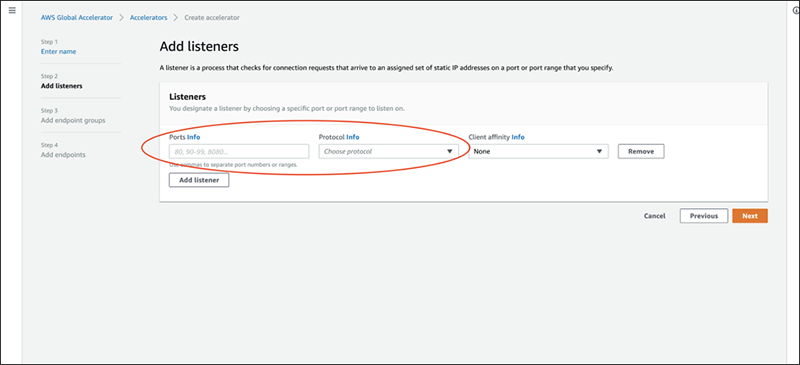
In the endpoint groups, we will choose Tokyo region since the ALB we will be attaching to is in Tokyo region. Other options will be set to default.
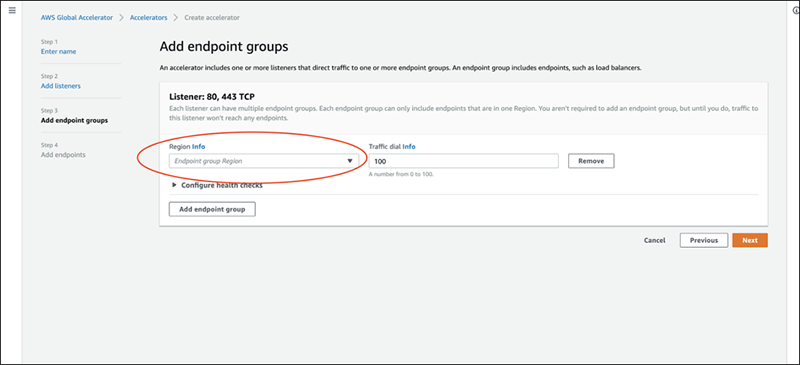
For the endpoint, we've decided to use the existing ALB. Select Application Load Balancer for [Endpoint type] and choose the existing ALB for the [Endpoint].
The [Preserve client IP] is checked by default, which is the key feature to store client IP.
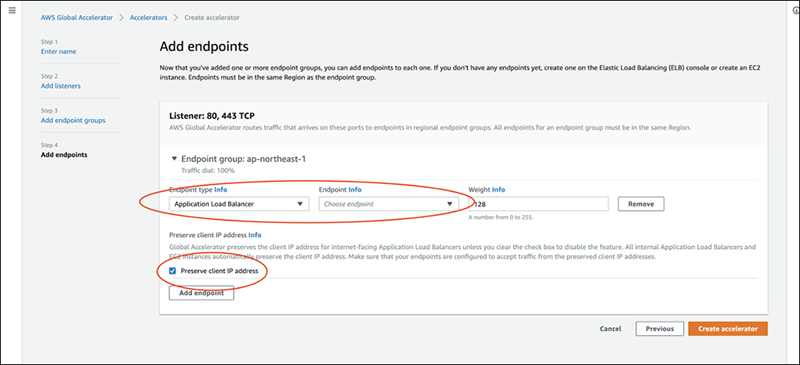
Configuration is complete.
4. Testing results
Let's compare recent direct access to ALB and access from AWS Global Accelerator in the ALB's access log. ALB will be accessed via FQDN and AWS Global Accelerator will be accessed via IP address.
Results
Access to AWS Global Accelerator IP address
http 2019-11-01T07:00:11.711762Z app/XXXX/e70c78dba838c0ab 153.156.XXX.XXX:25324 10.1.1.67:80 0.009 0.003 0.000 200 200 436 469 "GET http://13.248.XXX.XXX:80/health HTTP/1.1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - - arn:aws:elasticloadbalancing:ap-northeast-1:358486443100:targetgroup/XXXX/f0870ad213e22824 "Root=1-5dbbd7fb-1ca82807de71d7b317d24d51" "-" "-" 0 2019-11-01T07:00:11.699000Z "waf,forward" "-" "-" "10.1.1.67:80" "200"
Access to ALB's FQDN
http 2019-11-01T07:01:28.820837Z app/XXXX/e70c78dba838c0ab 153.156.XXX.XXX:25581 10.1.1.67:80 0.044 0.003 0.000 200 200 471 469 "GET http://XXXXXX.ap-northeast-1.elb.amazonaws.com:80/health HTTP/1.1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - - arn:aws:elasticloadbalancing:ap-northeast-1:358486443100:targetgroup/XXXX/f0870ad213e22824 "Root=1-5dbbd848-8987b080731e370036a91ec8" "-" "-" 0 2019-11-01T07:01:28.773000Z "waf,forward" "-" "-" "10.1.1.67:80" "200"
Since both accesses are logged in the ALB's access log, we can see that access from AWS Global Accelerator can reach the ALB.
Next, we create a rule to block the client IP address "153.156.XXX.XXX" and apply WAF to ALB.
*Refer to the blog post below on how to create a rule on WAF.
Block Attacks from Specific IP Addresses in AWS WAF
Results
Access to AWS Global Accelerator IP address
http 2019-11-01T07:17:51.351074Z app/XXXX/e70c78dba838c0ab 153.156.XXX.XXX:27880 - -1 -1 -1 403 - 553 689 "GET http://13.248.132.169:80/health HTTP/1.1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - - arn:aws:elasticloadbalancing:ap-northeast-1:358486443100:targetgroup/XXXX/f0870ad213e22824 "Root=1-5dbbdc1f-9309a030b09cbc80cff4a7b0" "-" "-" -1 2019-11-01T07:17:51.338000Z "waf" "-" "-" "-" "-"
Access to ALB's FQDN
http 2019-11-01T07:15:09.219543Z app/XXXX/e70c78dba838c0ab 153.156.XXX.XXX:27555 - -1 -1 -1 403 - 588 689 "GET http://XXXXXX.ap-northeast-1.elb.amazonaws.com:80/health HTTP/1.1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - - arn:aws:elasticloadbalancing:ap-northeast-1:358486443100:targetgroup/XXXX/f0870ad213e22824 "Root=1-5dbbdb7d-c9c77d42caaa39d06877f672" "-" "-" -1 2019-11-01T07:15:09.179000Z "waf" "-" "-" "-" "-"
We can see that the requests were blocked by WAF.
Below is the result of another AWS Global Accelerator without preservation of client IP address. The requester IP address was listed as reserved IP address from AWS Global Accelerator, meaning that the IP address filter was not applied and the access was deemed normal.
*Existing AWS Global Accelerator endpoint setting did not have a menut to edit "Preserve client IP" option, so we configured another AWS Global Accelerator and attached it to the same ALB.
*IP addresses are masked, but the accessed IP address of AWS Global Accelerator (the part colored in red) is different, but the client IP addresses is the same.
If client IP address is not preserved
http 2019-11-01T08:03:50.939611Z app/XXXX/e70c78dba838c0ab 13.248.XXX.XXX:49408 10.1.1.67:80 0.043 0.001 0.000 200 200 436 469 "GET http://13.248.XXX.XXX:80/health HTTP/1.1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - - arn:aws:elasticloadbalancing:ap-northeast-1:358486443100:targetgroup/XXXX/f0870ad213e22824 "Root=1-5dbbe6e6-515e5ec072200370775a77a0" "-" "-" 0 2019-11-01T08:03:50.683000Z "waf,forward" "-" "-" "10.1.1.67:80" "200"
If client IP address is preserved
http 2019-11-01T08:04:39.069937Z app/XXXX/e70c78dba838c0ab 153.156.XXX.XXX:34345 - -1 -1 -1 403 - 553 689 "GET http://13.248.XXX.XXX:80/health HTTP/1.1" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - - arn:aws:elasticloadbalancing:ap-northeast-1:358486443100:targetgroup/XXXX/f0870ad213e22824 "Root=1-5dbbe717-d76cbc38f263b6f003c13b24" "-" "-" -1 2019-11-01T08:04:39.057000Z "waf" "-" "-" "-" "-"
5. Conclusion
Because client IP address can be preserved, you can apply AWS Global Accelerator to a ALB that has been attached to AWS WAF.




