This post was originally written in Japanese in the past.
Table of Contents
- 1. Introduction
- 2. How to use the feature
- 3. Configuration details with an example
- 4. Example usages
- 5. Caveat
- 6. Limitations on WafCharm
- 7. Conclusion
1. Introduction
On February 12th, 2021, a feature to specify keys and values of JSON content in a request body (referred to as JSON parser feature further on) was released in AWS WAF.
You could only inspect a whole request body until this release, but you can now specify and narrow down what to inspect, which could lessen unnecessary matches, further improving the accuracy.
In this post, we will take a look at configuration and usage examples.
*This feature is not available in AWS WAF Classic.
2. How to use the feature
Create a rule in the AWS management console.
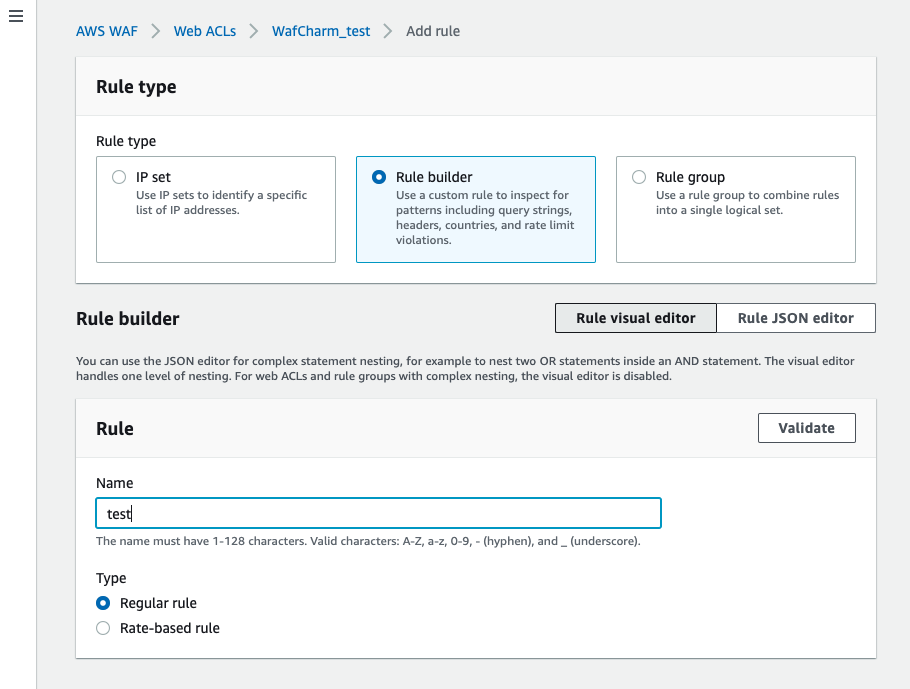
Choose from “Plain text” or “JSON” for a content type by selecting “Body” under the “Inspect” field, so select the “JSON” option.
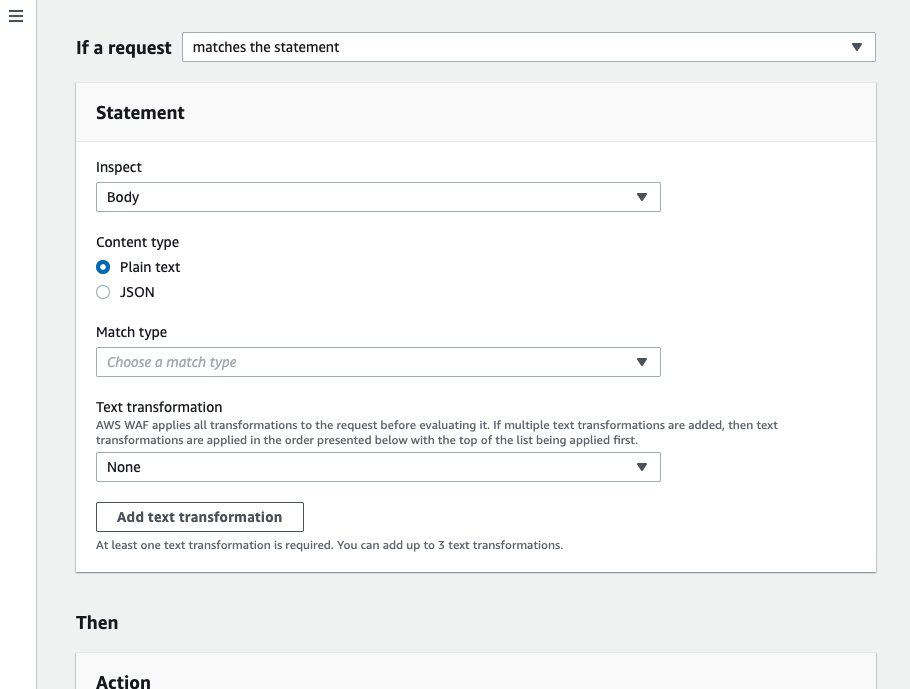
After selecting “JSON” for the content type, there will be more details shown to specify. Let’s take a look at them.
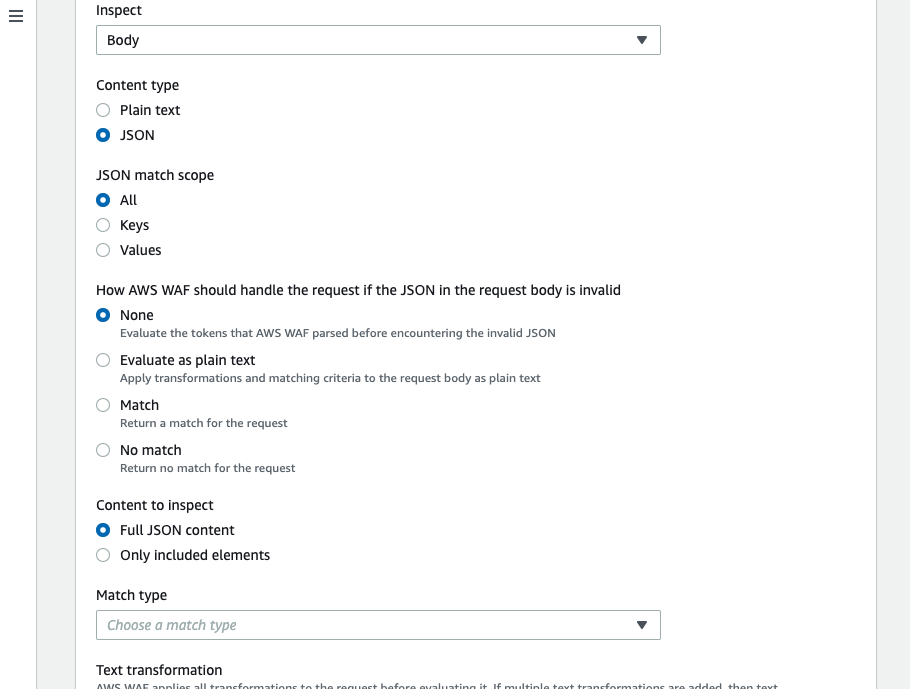
| Item | Description |
|---|---|
| JSON match scope | Select keys, values, or both (All) in this item. |
| How AWS WAF should handle the request if the JSON in the request body is invalid | Select the behavior when data did not match JSON format.
|
| Content to inspect |
There will be an input field if you select Only included elements. Specify content to inspect in the JSON Pointer syntax. |
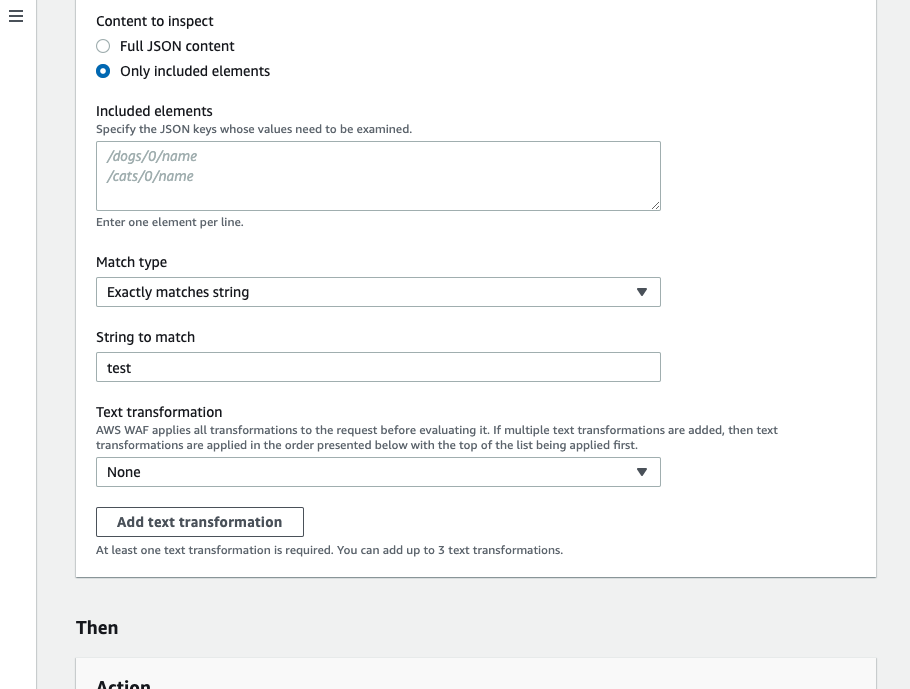
This is all for the configuration procedure. We will show an example for better understanding.
3. Configuration details with an example
We will look at an example JSON below for each configuration.
````
{
"user": {
"name": "Person Doe",
"data": {
"job": [
{
"role": "Engineers",
"position": "manager"
}
]
}
}
}
````
When separated into keys and values, it would look like the below.
| keys | user, name, data, job, role, position |
| values | Person Doe, Engineers, manager |
If JSON match scope is set to All, both keys and values will be inspected. By selecting Keys or Values, inspected content can be narrowed down to either of them.
As another example, when the Content to inspect is limited, the values listed below will be inspected.
| Content to inspect | JSON match scope | Inspected contents |
|---|---|---|
| /user/data | ALL | job, role, Engineers, position, manager |
| /user/data | keys | job, role, position |
| /user/data | values | Engineers, manager |
| /user/data/job/0 | ALL | role, Engineers, position, manager |
| /user/data/job/0 | keys | role, position |
| /user/data/job/0 | values | Engineers, manager |
JSON Pointer is defined by RFC6901.
Specify keys for associative array {} and specify placement for array [].
Reference:
https://tools.ietf.org/html/rfc6901
4. Example usages
| Change the setting to only inspect values | By limiting the content to inspect to inputs from clients, you could reduce the possibilities of false positives. |
| Only target to inspect where JSON structures change based on user input | By limiting the content to inspect, you could reduce the possibilities of false positives. |
| Exclude text input that accepts relatively free content from content to inspect | You could reduce the possibilities of false positives that could occur in relatively free text input *With increased scopes, higher WCU might be required. *This has to be edited in JSON editor. |
| Narrowing down the conditions of existing rules | You can narrow down the conditions of rules by combining JSON parser features’ conditions and existing rules using AND conditon |
Narrowing down to reduce false positives is beneficial if the content that does not get inspected is controlled and only accepts expected values. Use these methods after you’ve ensured that appropriate validation is provided.
5. Caveat
- AWS WAF request size limitations
AWS WAF can only inspect the first 8 KB (8,192 bytes) of the request body. In some cases, you have to combine rules to inspect based on request sizes.
- High cost
By using the JSON parser feature, usage of WCU increases to double the amount. It might be more cost-effective to implement methods to counter false positives by excluding certain URI paths than to exclude certain information in a specific JSON.
6. Limitations on WafCharm
Customization using the JSON parser feature is available.
Please refer to the AWS WAF document's JSON body section before requesting a customization.
You can add the rule as your own rule as well.
7. Conclusion
This feature can only be used for JSON format data, but it is useful to avoid false positives because you can narrow down the content to inspect.
However, having content not to inspect does pose security risks; ensure that your application has implemented a way to avoid unexpected value from being entered in a place you are excluding.



