【Table of contents】
- 1. Introduction
- 2. Handling False Positives Using the Rule Group Exception Feature
- 3. Demo
- 4. Changing WafCharm rule's actions
- 5. Conclusion
1. Introduction
In this article, we will show you how to set exceptions for individual rules from a rule group.
When a false positive occurs, you can exclude a specific rule from the rule group.
Excluding a specific rule does not mean deleting the rule, but changing the action of the rule to COUNT mode.
New feature: "Rule Group Exceptions" released to control individual rules in AWS WAF managed rules.
https://www.wafcharm.com/blog/aws-waf-managed-rule-rulegourp-exception-jp/
2. Handling False Positives Using the Rule Group Exception Feature
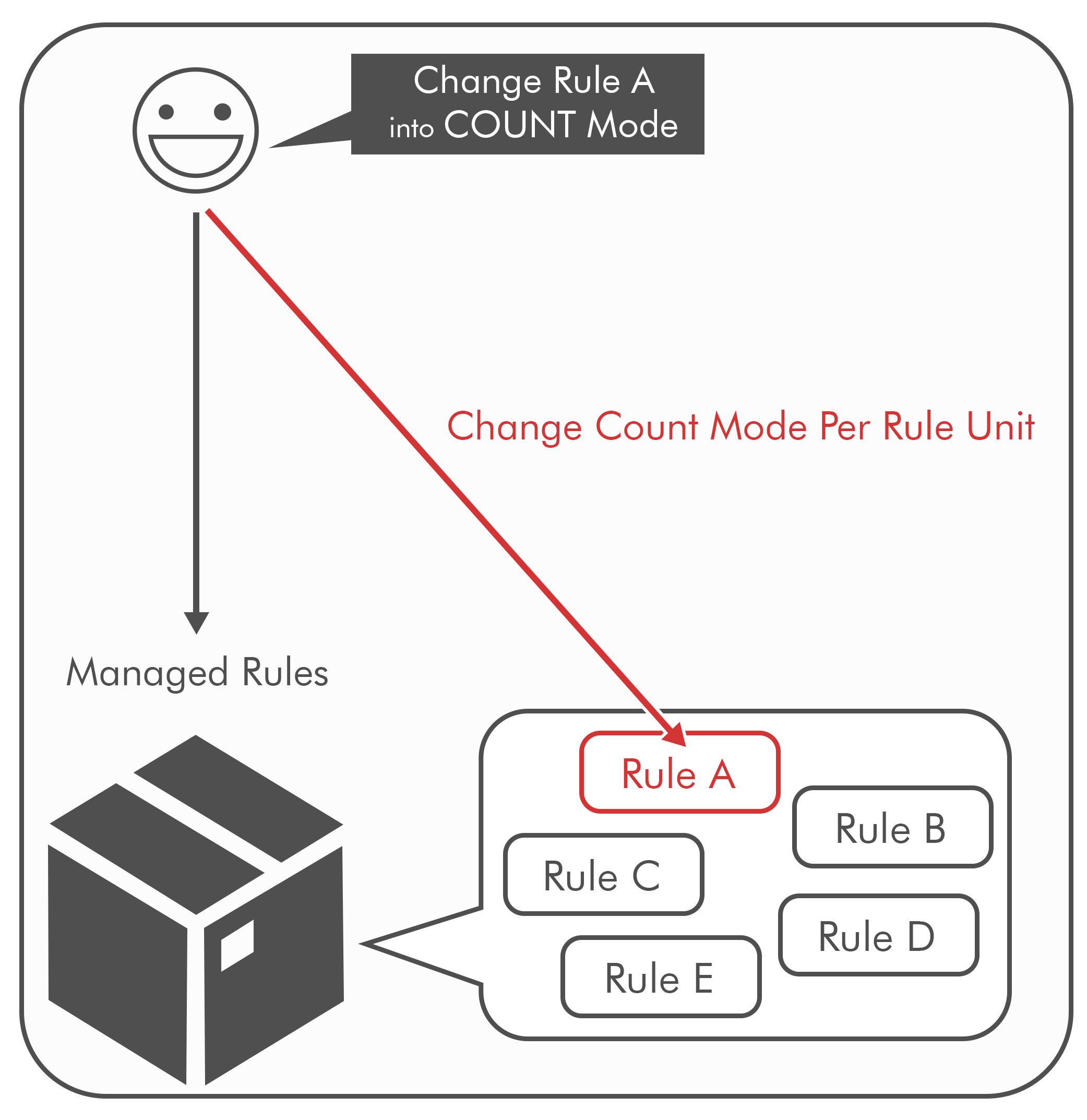
It is possible to change the specific rules to COUNT mode in a rule group where false positives have occurred.
By changing only the relevant rules to COUNT, we can minimize the defense capability loss rather than make the rule group to COUNT mode.
Here’s an illustration of how that works:
3. Demo
Request to be Detected
This time, we will use AWS-ManagedRulesCommonRuleSet as a sample, which is the ruleset published by AWS. We pickuped the rule "NoUserAgent_HEADER" to demonstrate changing the mode.
Please turn the managed rule and the rule to be BLOCK mode.
Now, we assumed that the bellow accesses is blocked by AWS WAF.
$ curl http://XXXXXXXXX.us-east-2.compute.amazonaws.com -A "" Result 403 forbidden
Configuring Exceptions for Rule Groups
Next, let's follow the steps to identify the detected rule names and set them to COUNT mode.
We will check the detection history, assuming that the WAF logs are being output to S3.
Step 1: Identify the rule name from the WAF log.
The detected rule name is listed in "terminatingrule."
In this case, we can read from the WAF log that "NoUserAgent_HEADER" was detected.
{
"timestamp": 1620866646423,
"formatVersion": 1,
"webaclId": "arn:aws:wafv2:ap-northeast-1:XXXXXXXXXXXX:regional/webacl/XXXXXXXXXXXX/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"terminatingRuleId": "AWS-AWSManagedRulesCommonRuleSet",
"terminatingRuleType": "MANAGED_RULE_GROUP",
"action": "BLOCK",
"terminatingRuleMatchDetails": [],
"httpSourceName": "ALB",
"httpSourceId": "XXXXXXXXXXXX-app/XXXXXX/XXXXXXXXXXXX",
"ruleGroupList": [
{
"ruleGroupId": "AWS#AWSManagedRulesCommonRuleSet",
"terminatingRule": {
"ruleId": "NoUserAgent_HEADER",
"action": "BLOCK",
"ruleMatchDetails": null
},
"nonTerminatingMatchingRules": [],
"excludedRules": null
}
],
"rateBasedRuleList": [],
"nonTerminatingMatchingRules": [],
"requestHeadersInserted": null,
"responseCodeSent": null,
"httpRequest": {
"clientIp": "XXX.XXX.XXX.XXX",
"country": "JP",
"headers": [
{
"name": "Host",
"value": "XXXXXX-XXXXXXXXXXXX.ap-northeast-1.elb.amazonaws.com"
},
{
"name": "Accept",
"value": "*/*"
}
],
"uri": "/",
"args": "",
"httpVersion": "HTTP/1.1",
"httpMethod": "GET",
"requestId": "1-609c7656-5b29d6e63add2bb82069a082"
}
}
Step 2. Change the Rule action of the Rule (NoUserAgent_HEADER) confirmed in Step 1.
Step2-1. Access the AWS WAF console (https://console.aws.amazon.com/wafv2/).
Step2-2. Click on “Web ACLs” > Select Applicable WebACL > "Rules" tab.
Step 2-3. Edit the corresponding managed rule from the list that appears.
Check the rule (AWS-AWSManagedRulesCommonRuleSet) and click "edit."
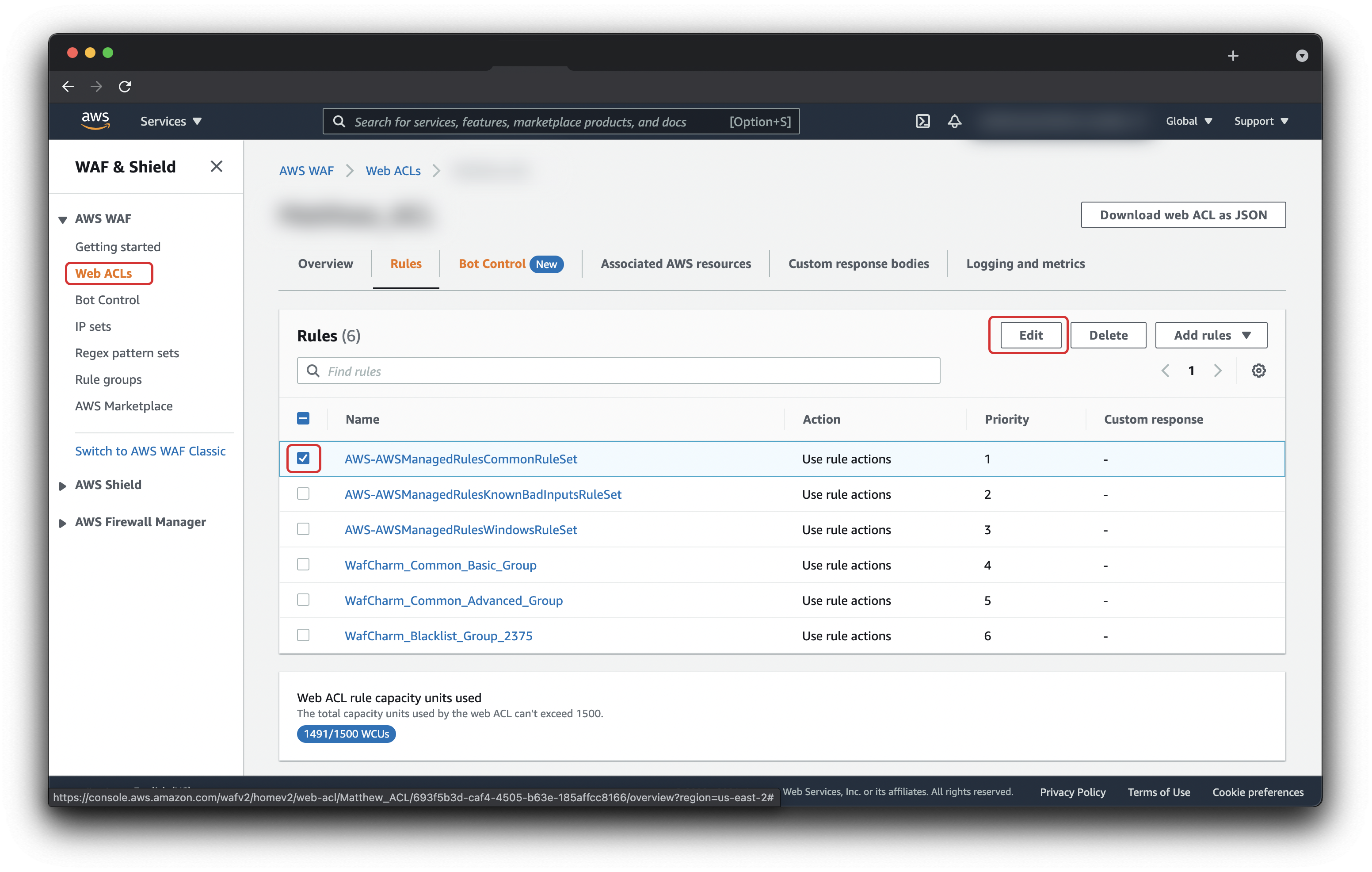
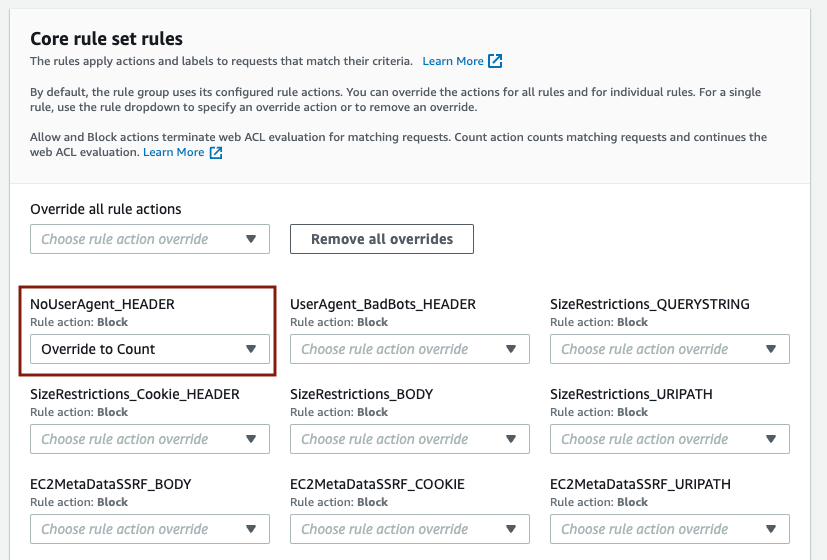
Step 2-4. Set the Rule action to Count.
Scroll downt to the section that shows the rule [NoUserAgent_HEADER]. Click on the pull down menu and select [Override to Count].
The following figure shows how the rule action has been set to Count.
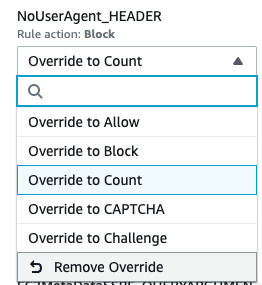
If you want to change the rule action back to Block, open the pull down menu again and click [Remove Override].
Step 2-5. Confirm the setting change.
Confirm that the settings have been changed to Count, and click "Save rule."
If you want to change the rule action of all rules, use the pull down menu under [Override all rule actions]. To remove the override, click the [Remove all overrides] button.
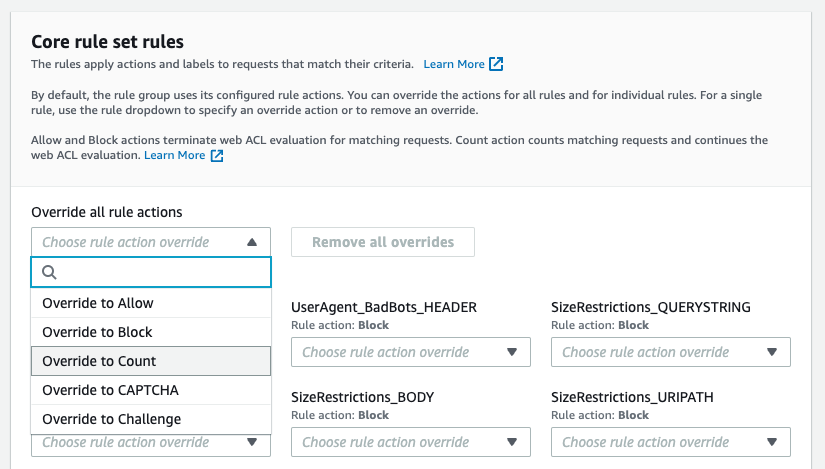
Check if the rule is Count mode
Let's see whether the intended behavior has been achieved.
Execute the request
curl http://XXXXXXXXX.ap-northeast-1.elb.amazonaws.com/ -A ""
The status code is changed to 403 forbidden to 200 OK.
Check the WAF logs.
You can see the rule "NOUserAgent_HEADER" is in "excludedRules" and the request is allowed by AWS WAF.
{
"timestamp": 1620868080953,
"formatVersion": 1,
"webaclId": "arn:aws:wafv2:ap-northeast-1:XXXXXXXXXXXX:regional/webacl/XXXXXXXXXXXX/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"terminatingRuleId": "Default_Action",
"terminatingRuleType": "REGULAR",
"action": "ALLOW",
"terminatingRuleMatchDetails": [],
"httpSourceName": "ALB",
"httpSourceId": "XXXXXXXXXXXX-app/XXXXXX/XXXXXXXXXXXX",
"ruleGroupList": [
{
"ruleGroupId": "AWS#AWSManagedRulesCommonRuleSet",
"terminatingRule": null,
"nonTerminatingMatchingRules": [],
"excludedRules": [
{
"exclusionType": "EXCLUDED_AS_COUNT",
"ruleId": "NoUserAgent_HEADER"
}
]
}
],
"rateBasedRuleList": [],
"nonTerminatingMatchingRules": [],
"requestHeadersInserted": null,
"responseCodeSent": null,
"httpRequest": {
"clientIp": "XXX.XXX.XXX.XXX",
"country": "JP",
"headers": [
{
"name": "Host",
"value": "XXXXXX-XXXXXXXXXXXX.ap-northeast-1.elb.amazonaws.com"
},
Changing WafCharm rule's actions
You can follow the step in Step2-4 to change the rule actions of the WafCharm rules.
Please keep in mind that WafCharm rules are structured to match requests that contain what seems to be an attack and block the request. You can choose other actions like Allow and CAPTCHA, but if you choose Override to Allow, the requests that are meant to be blocked will be allowed.
In addition, WafCharm rules are intended to work with COUNT/BLOCK actions, so other actions like CAPTCHA and Challenge may not work as intended.
Ensure you are not changing WafCharm rules to actions other than COUNT/BLOCK.
5. Conclusion
The rule group exception settings are listed in the AWS WAF navigation screen, which makes it easier to understand.
Hopefully, this guide will give you the confidence to configure the rules during an emergency.




